| Debt and Borrowing | Financial Goals | Virtual Assets | Cautions of Online Fraud | Wise Usage of Electronic Payment | Digital Financial Management | Further Readings |
Debt and Borrowing
 There are different types of financial institutions and finance companies in Hong Kong that provide a wide variety of loan products. Some people borrow to achieve financial goals, such as property mortgages, while others borrow for pleasure and consumption. However, if not properly managed, debt can quickly spiral out of control. Borrowing should never be taken lightly — it requires careful consideration and planning.
There are different types of financial institutions and finance companies in Hong Kong that provide a wide variety of loan products. Some people borrow to achieve financial goals, such as property mortgages, while others borrow for pleasure and consumption. However, if not properly managed, debt can quickly spiral out of control. Borrowing should never be taken lightly — it requires careful consideration and planning.
-
What is borrowing?
-
Types of Loans
-
Secured loans
A secured loan involves a borrower pledging assets such as property, deposits or stocks as collateral in return for the money borrowed. As secured loans are backed by collateral, they typically offer lower interest rate compared to unsecured loans. However, if the borrower fails to meet the repayment obligation, the lender has the right to seize and sell the collateral to recover the debt. If the proceeds from the sale do not fully cover the outstanding amount, the borrower is still liable for the remaining balance. -
Unsecured loans
An unsecured loan allows borrowers to obtain credit without providing collateral. Common examples of unsecured loans include credit cards, personal loans, tax loans and overdraft facilities. When applying for an unsecured loan, lenders review factors such as the applicant’s income, existing debt obligations, and credit reports and scores. Since these loans are not backed by collateral, they usually come with higher interest rates compared to secured loans.
-
Secured loans
-
Cost of borrowing
Interest is the primary expenses of taking out a loan. Borrowers should understand whether the loan carries a fixed or floating rate of interest. Different loan products adopt different methods of interest calculation. For example, personal instalment loans often apply either a monthly flat rate or an annual rate, while credit card outstanding balances are usually subject to daily or monthly compounding interest.
However, the total cost of a loan is not limited to interest. Other charges, such as handling fees or annual fees, may also apply. Therefore, both interest and related fees must be considered when calculating the overall cost of borrowing.
To help borrowers make effective comparisons of the actual cost of different loan products, financial institutions are required to adopt a consistent set of standards and assumptions when disclosing the Annualised Percentage Rate (APR). The APR is an annualised reference rate that combines both the basic interest rate and all associated fees and charges, giving a more accurate reflection of the actual cost of borrowing.
Reference:
IFEC - Loan basics -
-
Responsible borrowing
Assessing the necessity of borrowing
- Borrow only when absolutely necessary: Loans should not be used to satisfy discretionary spending. Borrowing does not increase your actual purchasing power and can lead to long-term financial obligations due to ongoing principal and interest repayments.
- Never borrow beyond your means: Before taking a loan, use the Borrowing and Debt Calculator to assess monthly repayments, loan term, and total borrowing cost. If you cannot afford the monthly repayments, do not borrow. Avoid taking out new loans to pay off existing debts, as this will only worsen your financial situation.
- Avoid reckless borrowing, even if you believe you can repay: Repaying loans is often more challenging than anticipated. Regular principal and interest payments can strain your finances, and habitual borrowing can lead to serious financial difficulties.
When considering taking out a loan, keep these key principles in mind:
Reference:
IFEC - Responsible borrowing
IFEC - To borrow or not to borrow? There are three criteria to consider
IFEC - Borrowing and Debt Calculator -
Proper debt management
-
Credit report
A credit report provides an overview of an individual’s credit and repayment history. It contains information on outstanding debts, bankruptcy, other public records (such as debt collection), and records of enquiries made by banks or financial institutions over the past two years.
Repayment history is the key factor in determining your credit score because it shows how well you manage your finances. Late or missed repayments—even just a few days overdue on a credit card bill--can negatively affect your credit score.
-
Maintaining a good credit score
A good credit score is important to everyone. It can help you secure loans at a better interest rates; in contrast, a poor score may result in higher interest charges or even rejection of your application. Additionally, many employers check credit reports to assess a candidate’s sense of financial responsibility.
-
Here are some tips to maintain a good credit score:
.Review your budget and financial situation to understand your borrowing and repayment ability.
.Pay all your bills on time every month.
.Avoid over-borrowing. Borrow only what you can afford to repay.
.Avoid applying for multiple lines of credits simultaneously.
.If you encounter difficulties in repaying debts, inform your lender promptly to discuss alternative repayment options.
.Check your credit report regularly to ensure all information is accurate and up to date.
-
Getting out of debt
Debt problems can cause stress for both individuals and their families, so they should be dealt with as early as possible. Procrastination allows debt to grow like a snowball, making it difficult to manage. To escape the cycle of debt, follow these steps:
- Assess your debt: Collect details of all your outstanding loans, including the type of debt, interest rates, repayment terms, total amount owed, and monthly repayment obligations.
- Create a budget: Track your monthly expenses and cut unnecessary spending.
- Avoid new debt: Examine your spending habits. Think carefully before making purchases and distinguish between needs and wants.
- Set repayment goals: For debts without fixed repayment reschedules, such as credit cards or revolving loans, set specific repayment targets based on your repayment ability to reduce interest costs.
- Pay off high-interest debt first: Prioritise paying off debts with the highest interest rate, especially credit card balances, to reduce your overall financial burden.
- Repay on time: Always make repayments on schedule. Late payments not only result in penalty fees but also damage your credit score.
Reference:
IFEC - Credit reports
IFEC - 6 ways to get out of debt
IFEC - Point to note when using a debt consolidation loan -
-
Beware of loan fraudsters
-
Recognize common tactics of financial intermediary scams
.Claiming they can help you obtain low-interest loans.
.Promising that you will not be charged any fees if your loan application is unsuccessful.
.Offering to help repay your other debts while processing your loan application.
.Impersonating bank staff or government officials, alleging problems with your existing loans or mortgage, and offering to “restructure” them for you.
-
Tips to avoid scams
.Do not trust a caller’s identity at face value. If someone claims to represent a bank, finance company, or government department, contact the organisation directly to verify their identity. Legitimate bank staff will never ask customers to borrow from other finance companies to repay existing loans.
.When seeking a loan, always use banks or reputable financial institutions.
.Avoid receiving loan funds in cash; opt for cheque or bank transfer instead, and keep all records.
.Carefully read and fully understand all contract terms and details before signing.
.If you encounter a suspicious intermediary or suspect a scam, report it to the police immediately.
Reference:
IFEC - Know more about loan intermediary scams
IFEC - Are intermediaries really helping you to secure loans? Or are they eyeing your money? -
-
Videos

IFEC – “The Chin’s Fairy Tale” - The “Loan-ly” Prince

IFEC – “The Chin’s Fairy Tale” – The Emperor’s Clothes is Full of Loans

IFEC – “The Chin’s Fairy Tale” – Chin-derella

IFEC - Good Debt VS Bad Debt - Credit card debts (Cantonese only)

IFEC - Good Debt VS Bad Debt - High risk investments (Cantonese only)

IFEC - Good Debt VS Bad Debt - Get your finances ready for life events
-
Think about this
- What negative consequences can have on young people who borrow for consumption?
- In your opinion, how important is it to have a personal credit report, and why?
- Why is it crucial for young people to understand the implications of debt issues at an early stage?
- Do you think including the warning “You have to repay your loans. Don't pay any intermediaries.” in loan advertisements is sufficient to heighten public vigilance against financial intermediary scams?
-
Further Reading
Please click here to read more related information.
Financial Goals
 A survey conducted by the IFEC at the end of 2018 revealed that it is common for the ‘Post 90s’ generation to set only short-term financial goals, with around one-third of respondents felt that their current financial situation hindered their ability to achieve any of their goals. Even though 53% of respondents had set financial goals, more than half admitted experiencing delays in reaching them. Underscores the challenges of setting and actively achieving financial goals! With the rapid development of technology, how should young people leverage digital tools to enhance their financial planning?
A survey conducted by the IFEC at the end of 2018 revealed that it is common for the ‘Post 90s’ generation to set only short-term financial goals, with around one-third of respondents felt that their current financial situation hindered their ability to achieve any of their goals. Even though 53% of respondents had set financial goals, more than half admitted experiencing delays in reaching them. Underscores the challenges of setting and actively achieving financial goals! With the rapid development of technology, how should young people leverage digital tools to enhance their financial planning?
-
Financial planning for life

Is financial planning important to me?
Financial planning is an important life-long skill that helps us to set, plan, achieve and review our life goals. Throughout different stages of life, it is essential to consider our current financial situation and future needs, such as planning for further studies, buying a home, starting a business, etc., in order to effectively manage various expenses and emergencies. Financial planning is not a once-and-for-all arrangement. When life circumstances or the overall economy and financial landscape changes, it is vital to revisit and modify our financial plans in a timely manner to ensure we stay on track to achieve our desired goals.
I don’t know how to do financial planning
Drawing up a basic financial plan involves just six key steps:
- Assess your financial situation: Begin by determining your net worth. List all your assets, such as your bank savings, investments, insurance products, etc., and subtract any outstanding debts.
- Create a budget: Managing your income, spending and savings is essential for improving your financial habits. By creating a budget, you can cut down on non-essential and impulsive spending while increasing your savings. You can use tools such as mobile apps and personal calculators to track your income and expenses, create a personal budget, and review your records at any time.
- Set your financial goals: Establish specific, clear and pragmatic financial goals based on your life aspirations, such as travelling, pursuing further education, or starting a business. Categorize your goals into short-term, medium-term and long-term according to their urgency and feasibility, as well as your personal financial situation and budget.
- Know your risk tolerance: Your financial plan will likely involve investments, and understanding the associated risks is crucial for achieving your expected returns. Before making any investments, consider your financial situation, the financial goals and timetables you have set, and your comfort level with potential losses. Once you understand your risk tolerance, you can start to create a portfolio that aligns with your financial goals and grow your wealth effectively by choosing the right investment instruments.
- Work out and implement a basic financial plan: A holistic financial plan encompasses not only investing and building your wealth, but also managing everyday spending and buying suitable insurance. Taking action is essential to achieving your financial goals. For young people, the first step in starting a financial plan is to establish a regular savings habit in order to benefit from the power of compound interest.
- Regularly review your plan: It is crucial to maintain discipline in following your financial plan. Periodically review your budget to make sure it remains effective, and regularly assess your financial plan. Adjust it as needed when your resources, needs and circumstances change to stay on track toward your goals.
Reference:
IFEC - Financial planning primer
IFEC - Designing a basic financial plan
IFEC - Getting started with investing -
Utilize wealth management tools
IFEC Money Tracker
The mobile app provides functions such as managing income and expenses, creating financial budgets for life events, setting savings goals, and calculating the time required to achieve them. It allows you to effectively manage your expenses and income, create budgets, and establish and track your savings goals.
IFEC Savings Goal Calculator
The online calculator helps you calculate how much you have to save every month to achieve your savings goal. It can also compute how long it will take to achieve your goal if you plan to make regular contributions to your savings.
IFEC Cut Back Calculator
The online calculator helps you in prioritising your spending and identifying unnecessary expenses to cut back on, making it easier for you to save.
Reference:
IFEC - Money Management Toolkit for Secondary Students
IFEC - Savings made easy with five simple tips -
Videos

IFEC - Start financial planning early

IFEC - Good budgeting helps you grow wealth

IFEC - Dreams, ideals or fantasies? (Chinese only)

IFEC - Between ‘ideal’ and ‘reality’ (Chinese only)
-
Think About This
- What are the major life stages you will face in the future?
- How would you set financial goals for different life stages?
- What strategies do you think will help you achieve your financial goals effectively?
-
Further Readings
Please click here for more information.
Virtual Assets
 Virtual Asset is a digital representation of value which may be in the form of digital tokens (such as utility tokens or security and asset-backed tokens), any other virtual commodities, crypto assets, or other assets of essentially the same nature. Virtual assets can serve multiple purposes, such as being a means of payment, an investment vehicle to generate current or future earnings, or provide access to a product or service. They may also fulfill a combination of any of these functions.
Virtual Asset is a digital representation of value which may be in the form of digital tokens (such as utility tokens or security and asset-backed tokens), any other virtual commodities, crypto assets, or other assets of essentially the same nature. Virtual assets can serve multiple purposes, such as being a means of payment, an investment vehicle to generate current or future earnings, or provide access to a product or service. They may also fulfill a combination of any of these functions.
-
What is “Virtual Asset”?
Emerging assets in digital form
Virtual assets exist solely in digital form and represent value that can be traded, transferred, or used for payment or investment purposes. Examples of virtual assets include crypto assets, decentralized autonomous organization tokens, non-fungible tokens (NFTs), and tokens claiming to be backed by commodities or other underlying assets. However, virtual assets do not include digital fiat currencies, such as the e-CNY issued by the People’s Bank of China.
Relationship with blockchain technology
Virtual assets are generally traded on blockchain technology, a decentralized system that operates without a central authority. In the case of Bitcoin, each participant connects to the bitcoin network via the internet and becomes a ‘node’ of the network. Transaction verification and records are sparsely stored in these independent nodes. During the transaction process, the nodes execute algorithms to validate and verify the transaction, adding the relevant data to the blockchain, which rewards a certain amount of bitcoin through a process known as ‘bitcoin mining’. Transaction data is organised into blocks and secured by cryptography. These new blocks are then linked chronologically to form a chain of blocks. All participants can view transactions on the blockchain but once a transaction is added, it cannot be modified or cancelled.
Highly speculative and risky
In recent years, various types of virtual assets, such as non-fungible tokens (NFTs), have emerged in the market and are evolving into alternative assets. These virtual assets exhibit significant differences in their characteristics and modes of operation. Many investors see virtual assets as speculative tools to capture potential massive short-term gains, increasing the market volatility of virtual assets.
Unlike traditional assets, virtual assets generally do not have any intrinsic value, nor are they backed by any government or financial institution. Their prices are primarily driven by investor confidence and market demand and supply, making them sensitive to market news. Besides, the user base and trading volume for many virtual assets are relatively small, which may lead to liquidity risk and potential for market manipulation. The digital nature of virtual assets are associated with various risks, including trading platform risk, cross-border risk, cyberattacks, wallet security issues, and concerns related to money laundering and terrorist financing. Furthermore, there has been a rise in virtual asset related scams, where fraudsters use virtual assets as bait to deceive individuals. Different jurisdictions may also have different regulatory stances on these emerging assets, with some virtual asset trading platforms unregulated or under minimal regulation, potentially leaving investors with insufficient protection.
Principles of investing virtual assets
Virtual assets are an emerging investment product with high risks. Their nature, modes of operation, and associated risks are significantly different from those of traditional investment products. It is therefore important for investors who wish to invest in virtual assets to thoroughly understand their features, operations and risks. Before investing, you should carefully evaluate your risk appetite and financial situation. If you do not fully understand virtual assets and cannot bear the potential losses, you should refrain from investing in this asset class.
Reference:
IFEC - Five things you should know about virtual assets
IFEC - Understanding the risks of virtual assets -
Careful drafting of investment plans
DYOR (Do Your Own Research) investment principles
Virtual assets have evolved over time and have accumulated impressive price increases in the past. Coupled with market sentiments, many investors become overly focused on the potential upside, overlooking the true nature and risks associated with virtual assets. If investors just follow the herd without understanding the products before investing, it is no different from gambling. The herd mentality and investing in unfamiliar products are big investment mistakes. Therefore, the virtual asset community often emphasizes the importance of DYOR (Do Your Own Research). This term has two meanings. Firstly, before investing in any virtual asset, investors should understand its nature, operations, and associated risks. Different types of virtual assets come with different features and risks. Hence, it is crucial to fully understand the product before making investment decisions. Secondly, in the age of social media, there are countless sources of investment advice, analysis, and news on virtual assets. DYOR also means not to follow the hype blindly. It is essential to conduct independent and critical research to make informed investment decisions.
Commonly seen crypto-related crimes
In cryptocurrency trading, the personal information or IP addresses of trading parties are not recorded on the blockchain, making cryptocurrencies highly anonymous and difficult in tracing the holdings. This anonymity has led to an increase in criminal activities, as perpetrators can conceal their identities and engage in money laundering. Below are some common crypto-related crimes:
- Online romance scams: Scammers build trust with victims and then fabricate different excuses, such as investment opportunities, gifts, or urgent need of cashflow, to ask for money in cryptocurrencies instead of cash to conceal their identities.
- Investment platforms: Scammers set up fake websites that direct victims to download mobile apps of fraudulent crypto-investment platforms through unofficial channels. Victims purchase cryptocurrencies through the app and transfer them to designated crypto wallets. Although victims may see their deposited funds grow on the fake website, this growth is illusory; in fact, their cryptocurrencies are in the hands of the scammers.
- ICO: Initial coin offering, or ICO, refers to the initial offering of new cryptocurrencies to fund investment projects. As investors expect huge profits in the future, they are often enticed to enroll in ICOs, which valuation is of low transparency. What’s worse is that some so-called ICOs are never issued.
- Robbery in face-to-face transactions: After completing a few small transactions with cryptocurrency buyers, criminals may claim to have larger amounts of cryptos for sale. Victims are lured to bring cash for a face-to-face transaction. Upon arrival, they are robbed of their cash, and the criminals flee. In some cases, criminals may impersonate as cryptocurrency buyers and lure victims into closing a deal in person, only to rob them of their cash after receiving the cryptocurrency.
- Ransomware: Criminals may hack into victims’ computer systems or introduce malicious code to encrypt files and databases. Victims are then forced to pay a ransom in cryptocurrencies to regain access their data.
Improving transaction security
Virtual asset wallets use private and public keys to protect and access virtual assets. The public key is the address of the virtual asset on the blockchain, similar to a bank account number; it can be publicly displayed to others for receiving virtual assets. On the other hand, the private key is the password that verifies ownership of the virtual assets, and only the holder of the private key can transfer their virtual assets to another address. A private key can generate the public key through algorithms, but the public key cannot be used in reverse to generate the private key. This helps ensure the security of the private key and, consequently, the virtual assets.
Virtual assets operate on decentralized systems without a central authority to keep record ownership. If a private key is lost or stolen, users may lose access to their virtual assets. Therefore, it is crucial for users to keep their private key safe and backed up.
Due to the length and complexity of private keys, some virtual asset wallets generate a set of "mnemonic", usually consisting of 12 to 24 words in English, making it easier to record and remember the key. A mnemonic is another form of private key and must be kept securely. Users are advised to save it in a handwritten form and store it in a safe place, and avoid storing it in the form of screenshots or photos to mitigate the risk of exposure.
Reference:
IFEC - DYOR is of utmost importance
IFEC - Beware of cryptocurrency scams
IFEC - Careful storage of virtual asset wallets and private keys
IFEC - Tips on investment and scam prevention for young people -
Test your investment personality
Investment decisions influenced by psychological factors
Many people invest significant time studying market trends, company fundamentals, and stock price charts, but they seldom understand the impact of their personalities on investment behaviour. Different personalities may associate with different behavioural biases that influence investment decisions. Common investment behavioural biases include:
- Herding: Investors tend to trust authority figures and follow the crowd, and are prone to join the bandwagon due to fear of missing out on potential gains.
- Risk aversion: Investors favour low-risk investments only, which may result in an overly conservative investment strategy.
- Overreaction: Investors who seek to closely track market trends may tend to react impulsively to market events, often leading to be short-term thinking and decisions.
- Overconfident: Overconfident investors may confuse their instinct as objective analysis, causing them to overlook changing market conditions.
- Expectations of high returns: Investors may prioritise investments that promising high returns while neglecting to assess the associated risks.
Understanding the Big Five Personality Test
Investment psychologists and behavioural finance economists used the Big Five Personality Test (Big5 test) to conduct research and found that personality is closely related to investment behavioural biases. For example, extroverts who are sentimental may be prone to herd mentality; introverts who value traditional wisdom are more likely to be risk-averse; people who are generally cheerful and well-organised are more likely to overreact to market events. Based on the Big Five Personality Test, the IFEC jointly worked with an academic team consisting of members from different local universities to develop a fun and interactive quiz with 10 questions closely related to everyday life. This quiz is designed to help you uncover your hidden investment personalities and behavioural biases. In addition to the test results and investment personality analysis, practical tips are provided to assist you in overcoming biases and fostering sound investment behaviour.
Reference:
IFEC - What is your investment personality? -
Videos

IFEC–‘Online Investment Strategy’ animation (Chinese only)

IFEC- How much do you know about virtual asset scams and risks? (Chinese only)

IFEC- Common tricks of virtual assets related scams

IFEC- What are the risks of unregulated virtual asset trading platforms? (Chinese only)

IFEC- What to look out for when investing in virtual asset? (Chinese only)
-
Think About This
- What reasons lead virtual asset investors to make poorly thought-out investment decisions?
- What must be considered before investing in virtual assets?
- How should young people set their investment strategies in light of the price volatility of virtual assets?
-
Further Readings
Please click here for more information.
Cautions of Online Fraud
 With the increasing maturity of financial technology and the widespread use of smartphones, people are actively engaged in various online consumption and financial activities, such as banking, investing, and shopping. As e-commerce and online investment activities continue to grow, scammers have found ways to engage in fraudulent activities. These include social media scams, phishing scams, and impersonation of investment advisers promoting “ramp and dump” schemes on social media. The forms of fraud are constantly evolving, and the risk of falling victim to scams is increasing. While technology advancement has made financial management and consumption more convenient, it is important for individuals to be aware of the associated risks and remain vigilant against common online scams.
With the increasing maturity of financial technology and the widespread use of smartphones, people are actively engaged in various online consumption and financial activities, such as banking, investing, and shopping. As e-commerce and online investment activities continue to grow, scammers have found ways to engage in fraudulent activities. These include social media scams, phishing scams, and impersonation of investment advisers promoting “ramp and dump” schemes on social media. The forms of fraud are constantly evolving, and the risk of falling victim to scams is increasing. While technology advancement has made financial management and consumption more convenient, it is important for individuals to be aware of the associated risks and remain vigilant against common online scams.
-
Common Online Scams

Romance Scam
Scammers often claim to be professionals from Europe, America, or working in Southeast Asia, and they search for targets on social media. After getting to know the victims, they initiate a pursuit and quickly establish an online romantic relationship without ever meeting in person. The scammers then use various excuses, such as needing to pay significant medical expenses or requiring urgent cash flow, to deceive the victims into giving them money. Additionally, some scammers establish ambiguous relationships with the victims and use fake investment platforms to entice them into participating in investments. Initially, the victims may earn a small return, but they suffer significant losses when more funds are invested.
Online Shopping Fraud
Online platforms for shopping and selling second-hand items have become popular due to their convenience. However, based on police statistics from the past five years, there has been a consistent rise in online shopping fraud cases. Scammers may impersonate sellers to attract unsuspecting victims by imposing purchase limits, providing discounts, or offering to purchase items on behalf of customers from other regions. After receiving payment from customers, scammers typically vanish and sever all communication. Alternatively, they may assume the role of buyers and fabricate false payment records, such as counterfeit deposit receipts or invalid cheques, to deceive sellers into releasing the goods. Once they obtain the items, they disappear and sever all contact.
Online Employment Fraud
Scammers use various online social media platforms or instant messaging apps to post job advertisements to attract job seekers. These recruitment ads often promoting enticing features such as high salaries, same-day payment, or work-from-home opportunities. They deliberately have low requirements in terms of age, education, and work experience for applicants. However, these job postings intentionally omit crucial details such as the actual job position, responsibilities, company name or address. Scammers employ various excuses to deceive victims to make payments, such as fees or deposits, under the pretense of securing job opportunities. Once the scammer succeeds in obtaining the payment, they sever all contact.
WhatsApp Hijacking
Scammers employ deceptive tactics to hijack victims’ instant messaging apps, such as WhatsApp accounts and contact lists. Typically, scammers will impersonate the victims’ friends or family members and send messages requesting the victims to share the verification code of their WhatsApp account. They then use the victims’ phone number to log in and take over their WhatsApp account. Impersonating the victims, the scammers contact their friends and family, urging them to buy game point cards and share the serial numbers with the scammers.
Phishing SMS/Whatsapp Messages
Phising is a type of online fraud where scammers pose as banks, government departments or commercial organisations by sending fake SMS/WhatsApp messages. They entice individuals to click on fraudulent links that direct them to counterfeit websites. The aim is to deceive people into providing personal digital keys such as phone numbers, bank account or credit card information, and login passwords. If scammers obtain this information, they can impersonate you and gain unathorised access to your online banking or other digital financial service accounts, resulting in financial loss.
Stock Trading Scams On Social Media
On social media, scammers have created numerous stock trading groups or “stock classrooms” with the intention of running “ramp and dump” schemes, rather than engaging in genuine discussions with investors. These groups make false claims about offering exclusive tips and insider information supposedly sourced from experts. In order to attract more followers, some scammers even impersonate public figures such as financial experts and Key Opinion Leaders (KOLs) to create and manage these stock trading groups.
Reference:
IFEC - Beware of Online Scams -
Tips to Prevent Online Fraud

Don’t be Greedy
Whether it is an investment scam or a romance scam, individuals who fall victim to these scams often find themselves confused and vulnerable to the persuasive tactics of scammers. Phrases like “easy profits, high returns, low risk” are commonly used as bait in investment scams, luring unsuspecting individuals with false promises. However, it is important to recognise that there are no guaranteed profits or high returns in any investments. Scammers manipulate victims by creating a sense of urgency, pressing them to act quickly. When faced with requests involving money or personal information and feeling unsure how to respond, it is crucial to remain calm. Seek help from trusted people around you, as they may provide valuable insights and offer a clearer perspective. It is better to err on the side of caution and seek guidance than fall prey to scammer tactics driven by greed.
Exercise Caution and Verify
It is important to remain vigilant against scammers who may impersonate individuals you trust and contact you through phone calls, emails, or social media messages, requesting money or personal information. Always take the necessary steps to verify the person’s identity before taking any action. When accessing banking websites, emails, mobile apps, etc., be mindful of any suspicious visuals, hyperlinks, or attachments that may request sensitive personal information. It is advisable to follow official channels, exercise caution, verify information, and consult with trusted individuals to ensure protection against scams.
Safeguard Your Passwords
Passwords are important pieces of information that authenticate our identities, making them enticing targets for scammers and hackers seeking unauthorised access to our bank accounts, investment accounts, or social media profiles. To protect yourself, it is crucial to create strong and unique passwords, and change them regularly. It is advisable to use different passwords for each account and avoid storing them on easily accessible devices or locations. Safeguarding passwords is essential to reduce the risk of unauthorised access to your accounts.
Reference:
IFEC - Don’t Believe the Scammers -
Videos (With English Subtitles)

HKMA - Protect Your Personal Digital Keys.Beware of Fraudulent Links!

ADCC - Disclose the Secret of QR Code "Anti-Deception for All"

ADCC - Scam Encounter - Romance Scam cum Investment Fraud (Chinese only)

HKCERT - Be Cautious of Phishing Attacks. Do Not Open Emails From Unknown Sources
-
Think About This
- Victims of online scams come from different age groups, educational backgrounds, and occupations. Try to analyse the various reasons behind falling victim to scams.
- If someone fall victim to online scams, what are the consequences they may face?
- If you or your family or friends unfortunately fall victim to a scam, how would you handle it? What attitude would you maintain?
-
Further Readings
Please click here for more information.
Wise Usage of Electronic Payment
 Payment methods are gradually moving away from a cash-dominated model in today’s modern society, as an electronic payment revolution is sweeping across the city. This shift encompasses various aspects of daily life, including consumer payments, online shopping, bill payments, fund transfers, and investments. With the availability of smartphones, smartwatches and tablets, transactions have become simplified and more convenient than ever before. While enjoying the perks of electronic payments, it is crucial remain vigilant about the potential security risks and personal privacy issues that associate with electronic transactions. It is also important to strike a balance and prioritise security to ensure that convenience does not come at the expense of our personal information.
Payment methods are gradually moving away from a cash-dominated model in today’s modern society, as an electronic payment revolution is sweeping across the city. This shift encompasses various aspects of daily life, including consumer payments, online shopping, bill payments, fund transfers, and investments. With the availability of smartphones, smartwatches and tablets, transactions have become simplified and more convenient than ever before. While enjoying the perks of electronic payments, it is crucial remain vigilant about the potential security risks and personal privacy issues that associate with electronic transactions. It is also important to strike a balance and prioritise security to ensure that convenience does not come at the expense of our personal information.
-
Common Electronic Payment Methods
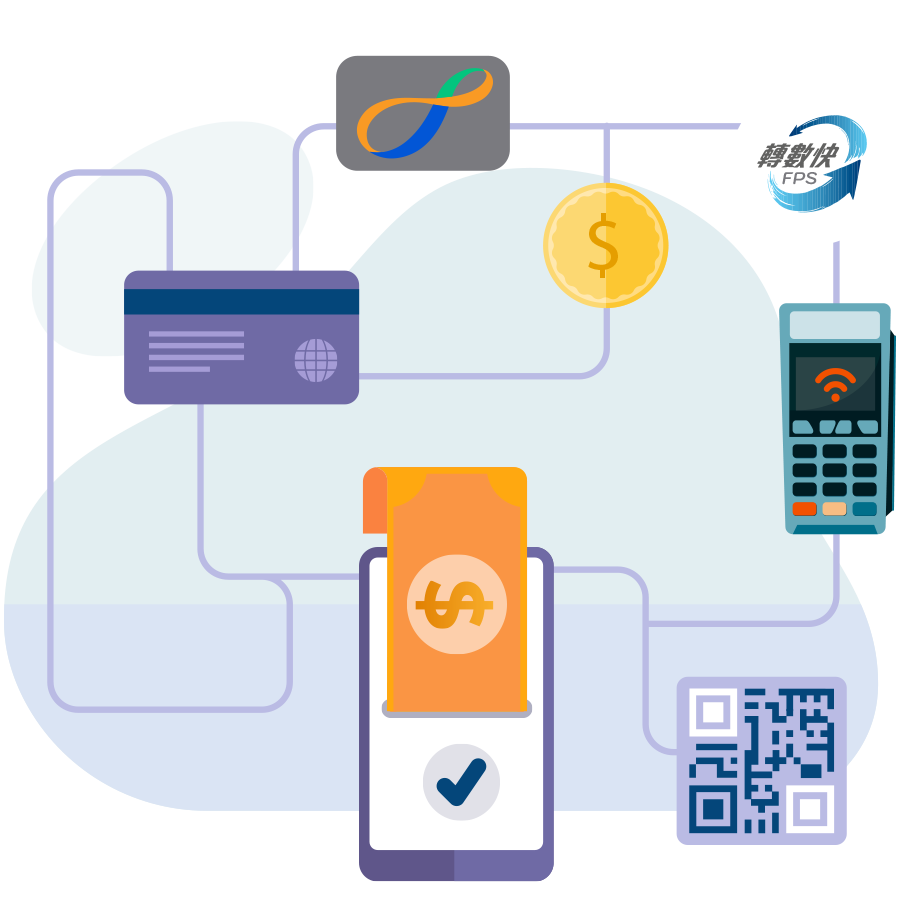
Credit Card
Credit cards are widely used as a primary payment for general consumption as they offer interest-free repayment periods and the convenience of cashless transactions. By ensuring that the balance is fully repaid by the due date, cardholders can avoid high interest and fees. However, if cardholders use cash advance to obtain cash from credit card, they have to pay interest and fees. It is important to note that credit card transactions are subject to terms and charges, so it is crucial to have a good understanding of the terms and conditions before using the service.
Debit Card
Debit cards operates differently from credit cards in terms of payment. When a debit card is used for a purchase, the corresponding amount is immediately deducted from the linked account, such as a savings account. It is necessary to ensure that there are sufficient funds in the linked account to complete the transaction successfully. The common types of debit card spending, including using an ATM card for EPS payments and using a bank-issued debit card for direct purchases.
Stored Value Facilities
Stored Value Facilities (SVF) refer to facilities which can store monetary value and can be classified into physical ones (e.g. Octopus Card) and non-physical ones (e.g. e-wallets). Similar to debit cards, SVF can be used for purchases as long as there are sufficient stored values available. SVF can be reloaded by making cash deposits or transferring funds. SVF can also link to a deposit account or credit card for direct debits during purchases.
Mobile Payments
Mobile payments are gaining popularity due to the rise of mobile devices such as smartphones and smartwatches. One of the most common type of mobile payments involves Near Field Communication (NFC) technology. NFC enables smartphones or smartwatches to communicate and exchange data packets with proximity card readers over very short distances. Apple Pay and Android Pay are the examples of mobile payments using NFC technology. Contactless payment offered by these mobile payments eliminate the need for physical credit cards or debit cards. This streamlined process enhances convenience and efficiency, speeding up the payment process for seamless experience.
Faster Payment System (FPS)
Introduced by the Hong Kong Monetary Authority, the FPS is a payment platform on which banks and SVF operators in Hong Kong are connected. It allows the public to make person-to-person (P2P) or person-to-merchant (P2M) fund transfers using online banking, mobile banking, or e-wallets. The FPS allows users to initiate transactions by simply using the payees’ mobile number, email address or QR code, providing convenience and accessibility anytime and anywhere. In addition to Hong Kong dollars, the FPS also supports transactions in Chinese yuan (Renminbi).
-
Ensure Secure Online Transactions

Be Vigilant for Cyber Security
Avoid using unfamiliar or insecure Wi-Fi networks in public places, and remember to disable Wi-Fi, Bluetooth or NFC functions on your device when not in use. Regularly update the operating system to ensure the security of your computer or mobile device used for online transactions. After completing an online transaction, always log out of the website or system and clear the data stored in the internet browser’s cache, cookies and browsing history.
Set Secure Passwords
Create strong passwords by using a combination of at least eight characters including a mix of letters and numbers. Avoid using the same password for multiple accounts and change your passwords regularly. Never share your password with anyone. Be cautious of phishing attempts or fraudulent emails or text messages requesting your login information. Banks and SVF operators never solicit personal information or ask for account passwords from their customers via email, phone calls or text messages.
Always Protect Your Personal Mobile Devices
By enabling automatic locking, installing reputable antivirus, anti-spyware, and anti-malware software, and configuring personal firewalls, you can maximise the protection of your computer or mobile device. Only download mobile apps from official app stores. Keep your device’s operating systems, apps, software, and browsers updated.
Knowing Your Payment Tools
Before using any mobile payment apps, it is important to thoroughly review their terms and conditions. Pay attention to details such as fees, privacy policies, and user rights and responsibilities. Different mobile payment apps operate using different mechanisms. Some may directly link to your bank or credit card account, while others may require preloading funds into the app.
Avoid Disclosing Confidential Information
Mobile payment tools may request access to data stored on your phone, such as contact information, location or photos. Service providers should seek your consent before accessing such data. Before granting access, you should consider your needs, circumstances and necessity of granting access before making a decision. When installing any software or apps on your computers or mobile devices, you should carefully consider security and privacy implications.
Pay Attention to Payment Details
When shopping online, it is crucial to assess the security of the website, particularly the login and payment pages. Look for indicators such as a padlock symbol in your internet browser’s address bar and ensure that the web address starts with “https”, indicating a secure connection. Consider printing or taking screenshots of transaction records. Avoid transferring funds, making direct deposits, or sharing bank or credit card information through email. Instead, use secure online payment methods that offer encryption and robust security measure. For example, using FPS or SVF to make direct payments to merchants.
Regularly Check Your Transaction Records
Making it a habit to regularly check your transaction records. Log in to your bank or credit card accounts or SVF periodically, or as prompted, and carefully review all transactions. By checking your transaction records frequently, you can promptly identify and address any unauthorised transactions that may have occurred.
References:
IFEC - Mobile Phones to Replace Cash
IFEC - Security Tips for Online Trading -
Videos (With English Subtitles)

HKMA - Avoid Mis-transfer of Funds. Check the Payment Details Carefully!

HKMA - P2P Small-value Funds Transfer Service (Chinese only)

HKMA - Stored Value Facilities

ADCC - Online Shopping Scam - Online Shopping Challenge
-
Think About This
- What are the advantages and conveniences of electronic payments? How do electronic payments benefit personal consumption and financial management?
- The convenience of electronic payment methods may contribute to an increase in online shopping activity. What strategies should teenagers adopt to avoid excessive spending?
- Is electronic payment suitable for all scenarios? In which situations is it more advisable to use cash or other payment methods?
-
Further Readings
Please click here for more information.
Digital Financial Management
 Technological advancement has created a stage for the development of “fintech”, which significantly enhances the operational efficiency and service levels of financial institutions through innovative technologies. The four major areas of fintech are artificial intelligence (AI), blockchain, cloud computing, and big data. As long as individuals have internet connectivity, financial management can become a simple task at their fingertips with fintech. However, since decisions can be made with a simple touch or swipe, and submitting information takes just a blink of an eye, it is even more important for individuals to remain vigilant in order to safeguard their personal privacy and rights. While embracing the digitisation of financial management, it is crucial to maximise security awareness at the meantime.
Technological advancement has created a stage for the development of “fintech”, which significantly enhances the operational efficiency and service levels of financial institutions through innovative technologies. The four major areas of fintech are artificial intelligence (AI), blockchain, cloud computing, and big data. As long as individuals have internet connectivity, financial management can become a simple task at their fingertips with fintech. However, since decisions can be made with a simple touch or swipe, and submitting information takes just a blink of an eye, it is even more important for individuals to remain vigilant in order to safeguard their personal privacy and rights. While embracing the digitisation of financial management, it is crucial to maximise security awareness at the meantime.
-
Four Major Areas of Fintech

Artificial intelligence (AI)
AI is capable of mimicking human intelligence and improving itself through “deep learning”. Deep learning is a subset of machine learning that simulates how the human brain learns, processes, and analyses massive amounts of data and information, ultimately generating and providing decision-making solutions. Taking robo-advisers as an example, their ability to select stocks or build investment portfolios often relies on investment theories and models. Another example is AI’s real-time calculation of network defence mechanisms, enabling it to prevent, detect, and respond promptly to attacks and threats, making it more efficient than other online systems.
Blockchain
Blockchain is a technology that supports various cryptocurrency transactions by providing a decentralised ledger and verifying transactions. Bitcoin is the most well-known application of blockchain technology. Through blockchain, every transaction conducted on the Bitcoin network is recorded anonymously in a publicly accessible ledger. Each new Bitcoin transaction is added to the blockchain. Different industries are eager to explore this emerging technology, including finance, energy, media and entertainment, and retail. In the finance industry, for example, traditional financial systems can utilise blockchain services to manage online payments, accounts, and market transactions, enhancing the efficiency of batch processing and manual reconciliation in financial transactions.
Cloud Computing
Cloud computing connects users to cloud platforms where they can apply for, and access rented computing services over the internet. Central servers handle all communications between client devices and servers for data exchange. This architecture typically includes security and privacy protection features to ensure the safety of relevant information when users only pay for their actual usage. An example of a cloud computing provider is Google’s Gmail, where users can access Google-hosted documents and applications from any device over the internet.
Big Data
Big data refers to a large volume of data collected from different sources and channels. Nowadays, businesses can gather first-hand data such as browsing behaviour through tracking technologies on websites and applications, as well as through the utilisation of IoT devices. This data is then analysed, for example, using AI algorithms to differentiate users based on their varying purchasing power. Based on their different purchasing capabilities, appropriate information and services can be provided to users. Due to the enormous scale of big data, an increasing number of companies are opting to collect and store data using cloud services, establishing a big data environment, and applying the results of data analysis to support business decision-making and planning.
References:
IFEC - Robo-advisers: Understanding the Investment Intelligence of A.I.
IFEC - Basic Concept - Blockchain -
Digital Financial Management Tools

Mobile Payment
Mobile payments are gaining popularity due to the rise of mobile devices such as smartphones and smartwatches. One of the most common type of mobile payments involves Near Field Communication (NFC) technology. NFC enables smartphones or smartwatches to communicate and exchange data packets with proximity card readers over very short distances. Apple Pay and Android Pay are the examples of mobile payments using NFC technology. Contactless payment offered by these mobile payments eliminate the need for physical credit cards or debit cards. This streamlined process enhances convenience and efficiency, speeding up the payment process for seamless experience.
Faster Payment System (FPS)
Introduced by the Hong Kong Monetary Authority, the FPS is a payment platform on which banks and SVF operators in Hong Kong are connected. It allows the public to make person-to-person (P2P) or person-to-merchant (P2M) fund transfers using online banking, mobile banking, or e-wallets. The FPS allows users to initiate transactions by simply using the payees’ mobile number, email address or QR code, providing convenience and accessibility anytime and anywhere. In addition to Hong Kong dollars, the FPS also supports transactions in Chinese yuan (Renminbi).
Virtual Assets
Virtual assets, also known as crypto assets, are digital forms of value that lack a physical presence. They can be used for trading, transfers, payments, and investments. Their value is derived from market demand and investor confidence, as they lack intrinsic value and do not have the support of governments, banks, or physical assets. As a result, virtual asset prices exhibit volatility, making them high-risk products. Moreover, virtual assets carry additional risks related to trading platforms, wallet security, and potential involvement in criminal activities. Investing in virtual assets should only considered by individuals who have a thorough understanding of this asset class and can tolerate the potential significant losses that may occur.
Virtual Banks
The major characteristic of a virtual bank is the digitisation of banking services, meaning there are no physical branches, and operations are primarily conducted through financial technology and the internet. Customers can access banking services anytime and anywhere. Virtual banks mainly serve retail customers, including small and medium-sized enterprises (SMEs), with a focus on retail banking services. In the initial stages of operation, a virtual bank may only provide basic banking services such as account opening, deposits, and loans. As virtual banks continue to evolve, they may expand their offerings to include other services and products. Each virtual bank adopts different business strategies, focus on specific development directions, and offer unique features. It is important for customers to carefully assess whether the services provided by a virtual bank align with their individual needs and preferences.
Robo-advisers
Robo-advisers generally refer to online platforms that use algorithms and data-driven strategies to provide financial advice. They collect information about clients’ age, financial goals, risk tolerance, investment horizon, and financial situation through online questionnaires. After analysing this data, they provide personalised investment recommendations that suits the clients’ risk level and financial objectives. In comparison to traditional human financial advisers, robo-advisers generally charge lower fees and have lower investment thresholds. They also provide round-the-clock financial advisory services, accessible as long as clients have internet connectivity.
Equity Crowdfunding
Equity crowdfunding is a common form of crowdfunding that enables investors to invest in projects or businesses, typically startups, through online platform. In exchange for their investment, investors receive equity shares in the company. Investors can browse equity crowdfunding platforms through internet or mobile apps to access summarised information of crowdfunding projects or companies.
Peer-to-Peer Lending (P2P lending)
P2P lending refers to a type of small-scale financing where online platforms or mobile apps act as intermediaries, connecting investors (lenders) with borrowers. These platforms leverage technology to streamline operations and reduce overheads, allowing them to offer loans with lower lending spreads compared to traditional financial institutions. P2P lending platforms offer various types of loans, including commercial loans and consumer loans.
References:
IFEC - Fintech and What You Need to Know
IFEC -"New Virtual Asset Trading Platform Regulatory Regime at a Glance -
Protect Your Personal Information
Keep Your Personal Digital Keys Safe
In the digital world, your account login and personal information are your personal digital keys. They are as important as the keys to your home. Examples of personal digital keys include online banking account number, login credentials, social media accounts, etc. Once these data fall into the hands of malicious individuals, they can impersonate you and gain unauthorised access to your online banking or other electronic financial service accounts, resulting in financial loss. It is important to avoid logging into online banking through unknown Wi-Fi networks or public computers; protect your computer and mobile devices; keep your operating systems, online banking apps, and browsers up to date; install and regularly update security software to defend against malware; and be cautious of suspicious files, websites, or opening unknown hyperlinks or attachments.
Take Confidentiality Measures Seriously
Cybercriminals employ extensive tactics to infiltrate computers and mobile devices to steal login credentials for online accounts and manipulate them for their own gain. Therefore, you should be cautious of social engineering traps such as phishing emails or text messages, avoid disclosing online account information and confidential data to others, and exercise cautions when posting personal information on social media. Regularly scan your computers and mobile devices for viruses, detect and promptly remove any malicious software. Set up strong passwords that are unique and unrelated to personal information, and include a mix of uppercase and lowercase letters, numbers, and symbols to increase the difficulty of password cracking. Regularly change passwords and avoid reusing the same password for different accounts. By implementing these defensive measures, you can mitigate the risk of unauthorised access to your personal data.
References:
HKMA - Personal Digital Keys
IFEC - Keeping Your Personal Details and Passwords Safe -
Money Management Tools for Youth
-
Videos (With English Subtitles)

HKMA - Protect Your Personal Digital Keys. Beware of Fraudulent Links!

HKMA - Don’t Use Unknown Wi-Fi and Safeguard Your Digital Keys
-
Think About This
- How can digital financial management help us in effectively establishing and achieving financial goals, including savings, investments, and retirement plans?
- How can teenagers prepare themselves to adapt to the rapid development of digital financial management?
- How can we assist relatives and friends in becoming familiar with the digital landscape and enjoying the convenience of digital financial management?
-
Further Readings
Please click here for more information.
Further Readings
As digital technology and fintech continues to evolve, it is essential to stay informed about the latest advancements and trends. In addition to this website, you can explore reliable sources to access up-to-date information on cyber security and digital technology.
-
Financial Goals
-
Debt and Borrowing
-
Virtual Assets
-
Cautions of Online Fraud
Anti-Deception Coordination Centre
Office of the Government Chief Information Officer - Cyber Security Information Portal
Hong Kong Monetary Authority - Beware of Fraudsters
Cyber Security and Technology Crime Bureau of the Hong Kong Police Force - CyberDefender
Consumer Council - Beware of Fraudsters in Social Media. Stay Alert to Stock Market Scams (Chinese only) -
Wise Usage of Electronic Payment
Hong Kong Computer Emergency Response Team Coordination Centre - Near Field Communication Security Guidelines
Hong Kong Monetary Authority - Smart Consumers
Hong Kong Monetary Authority - Safe Use of Stored Value Facilities
Consumer Council - Get To Know Your Data Protection Rights before Using Mobile Payment Services -
Digital Financial Management
